Just this past week a solution has finally emerged from reddit thanks to donkerslootn
(https://www.reddit.com/r/Fedora/comments/11qk9gx/luks_and_fido2_unlock_on_fedora_silverblue/)
on how to unlock an encrypted disk upon boot using a YubiKey (instead of a password) for the excellent Fedora Silverblue OS (both 37 and 38 beta worked).
By default, one would need to type in the password for the LUKS encrypted disk to unlock the disk and enable the OS to boot into the GNOME sign-in screen. Given the daily system updates to Silverblue (that require a reboot) all this typing gets repetitive and implies a weak password. Securing the GNOME sign-in with a YubiKey is already well documented. But to upgrade security from a typed in password for the LUKS disk to a YubiKey was problematic and the internet did not have a solution for months. Silverblue imposes its own requirements due to its immutable nature (so the conventional dracut method used normally in most Fedora distros (https://unix.stackexchange.com/questions/705795/fido2-yubikey-to-unlock-luks-at-boot-on-fedora-36-not-working) would not work).
- Fedora Silverblue should already be running with a LUKS encrypted disk
- a recent YubiKey is needed (YubiKey 5 works)
- the FIDO2 dracut module should be installed by default (to check,
dracut --list-modules | grep fido2is suggested and should returnfido2) - identify the /dev/ description for your LUKS encrypted disk partition (e.g., using the disks application)
- the usual cautions apply about changing your OS (backups, know what you are doing, etc…)
- setup the YubiKey on the Fedora Silverblue command line (note possible modifications):
sudo systemd-cryptenroll --fido2-device=auto --fido2-with-client-pin=true --fido2-with-user-presence=true /dev/nvme0n1p*
If you are running a device that doesn’t necessarily have a keyboard connected at boot, --fido2-with-client-pin=false works to only require that you touch the YubiKey without the need to enter the PIN. Note that /dev/nvme0n1p* will need to be substituted with your boot device name (check using the disks utility).
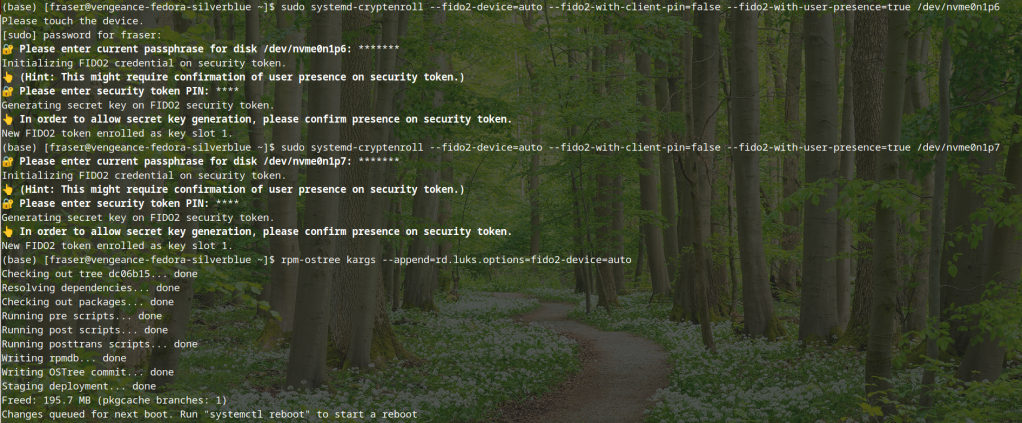
The command line will ask you to touch the device, enter the password for the LUKS disk, enter the YubiKey PIN (such as used on FIDO2 websites and when logging into Fedora Silverblue assuming you secured login with YubiKey already–not the YubiKey hardware PIN) and touch the device after entering the PIN and once again to confirm presence. It should then return New FIDO2 token enrolled as key slot 1 if this is your first YubiKey.
- add FIDO2 device to the rpm-ostree:
rpm-ostree kargs --append=rd.luks.options=fido2-device=auto
Once finished it suggests systemctl reboot to reboot but you can wait for the next step before rebooting.
- update initramfs:
rpm-ostree initramfs --enable --arg=--add --arg=fido2
This is the breakthrough that donkerslootn at reddit solved! Once that is done you can systemctl reboot. If all goes well, you should get a flashing YubiKey and a circulating wheel when Silverblue reboots past the BIOS. Touch the YubiKey (it should stop flashing), enter the PIN if you set the requirement to =true, and it should boot into the normal GNOME login screen.
I had been searching for a way to unlock the boot disk with a YubiKey using FIDO2 for months: thanks donkerslootn!
As an aside, if you find these guides helpful, please leave a like. I noticed a steady amount of traffic on these how-to guides (but very rarely do readers indicate they were helpful, which is weird).

